OpenKeychain 3

Release 3.0 of the OpenKeychain Android app is out today. I’m super-proud to have been a (minor) contributor. It’s getting pretty slick, if I say so myself; maybe almost civilian-ready. Read on for an explanation, with screencasts and geek notes too!
What it does · Your mobile device comes with a lot of different ways to exchange messages with other people over the Net. OpenKeychain can do three things:
Encrypt the messages, so only the The Right Person can read them.
Sign them, so that The Right Person knows who sent them.
Decrypt them for The Right Person to read, while checking the signature.
How do you send and receive these private messages? Whatever works for you: Gmail, regular email, your fave chat program. This is based on the Share Menus that every Android-carrying human has used for years. I hear that iPhones are getting general-purpose sharing too, so let’s hope for an iOS OpenKeychain equivalent soon.
Two big things that have really gotten in the way of Popular Cryptography have been first, how you go about finding people’s keys, and then, how do you do this stuff without having to type passphrases into a mobile device? OpenKeychain has plausible solutions to both those problems.
Key finding · If you want to exchange private messages with another person and be really sure nobody else can read them, you’ll need that person’s “public key”. Having your own is no problem; they’re free, and easy to make; but finding other people’s has been a problem.
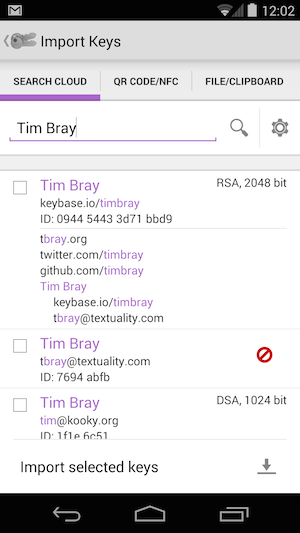
But if you know someone’s name or email address or Twitter handle or domain name, OpenKeychain can search the cloud for those things (it feels like searching Google) and if they have a key there’s a good chance it’ll find it, then you can load it into the app and start private messaging. [Disclosure: This is the part I worked on.]
It’s easier to show than explain; Here’s a little screencast (1 minutes 55 seconds).
That screencast highlights the other big problem; passwords.
Betcha can’t type this · When you make yourself a key, you actually get two: Public and private. To do this sort of secure messaging, you use other people’s public keys and your own private key. Just like the name suggests, it’s gotta be private. In practice, that means every time you use it, you have to type in a password; only they say “passphrase” because it should be specially long and hard for the bad guys to guess. Which is OK if you’re sitting in front of a nice modern keyboard, but essentially impossible on a mobile device.
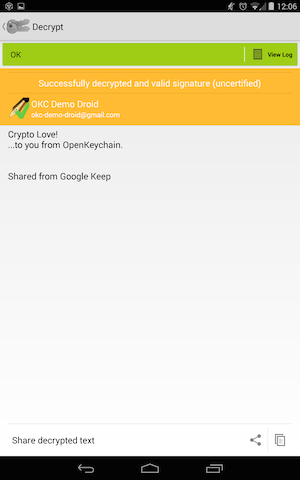
Here’s another little screencast (58 seconds) showing how that works. The key trick is that instead of unlocking your phone (“something you know”) and typing a passphrase (“another thing you know”), for the second step you slap a pocketable little crypto doohickey against the back of the Android (“something you have”).
In this case, the doohickey is a YubiKey Neo, but this is a growing market with standards creeping in, so I’m betting there’ll be lots of doohickey choices down the road. Hello-Kitty and Harley-Davidson branding any day now!
Anyhow, this is getting very close to being something anyone could use. The only thing that’s really wrong with this picture is that it should just be built into Gmail and Facebook and Slack and, well, anything you find yourself using to communicate with people.
Geek notes ·
The “Cloud search” hits Keybase.io and the traditional OpenPGP keyservers in parallel, and as soon as there are other public-facing key directories, for example Google End-to-end, it’ll search those too.
I had some real fun, because I got to do a little bit of Java-flavored shared-mutable-state thread wrangling for the parallel searches, the kind of thing I spent years at Sun telling everyone they should never do. Simple stuff, but it wouldn’t surprise me if there’s a subtle concurrency bug, and there wouldn’t be if I’d done it in Clojure or Go or Elixir.
What the Yubi actually does is generate an RSA keypair, only the private key part is empty, with a bit that says “Go ask the crypto dongle.” It’s integrated with GnuPG and reasonably easy to set up, and those keys work out-of-the-box with Keybase.io.
The Yubi/NFC implementation isn’t perfect. You’d like to have the Neo on an ordinary physical keychain but that makes it hard to lie flat on the back of the Android. Also, you need to place it pretty well right in the middle of the back, easy on a handset, a little tricky on a Nexus 7; and then not move it for a second or two.
Moving keys around, for example from your PC to your mobile, still isn’t civilian-ready. I had to use gpg to export my keypair and put it in DropBox, then OpenKeychain was happy to pick it up. I’m thinking that if the Yubi can generate it, the Yubi should bloody well be able to transfer it to the Android via NFC; but this remains work-in-progress.
Comment feed for ongoing:
From: Brent J. Nordquist (Oct 02 2014, at 18:22)
Out of curiosity, which PGP keyservers do you upload to these days? I recently refreshed my PGP key (before putting it on Keybase), and uploaded it to MIT and SKS, but I'm not sure if those are the right ones any more.
[link]
From: Tim (Oct 02 2014, at 18:54)
Brent: I think the keyservers are supposed to sync up with each other, so it shouldn’t matter that much.
[link]
From: Janne (Oct 02 2014, at 20:08)
How well does the yubi dongle work with laptops, desktops and other things without NFC? Is it standardized and open enough that it'll work on Windows, OSX and Linux alike?
Also, I got to thinking: You want to show that you have something other than your device. The Yubikey is another device to carry around; how about optionally or instead use any of your other regular devices?
So I could authenticate on my laptop with my phone - or on my phone with my laptop - through Bluetooth or USB cable or something; my phone and tablet could authenticate each other; or any other such combination.
So what you'd need is not one, specific device, but any pair of devices that are recognizably yours only.
[link]
From: Tim (Oct 03 2014, at 05:44)
Janne - You can set it up to work with 2-factor on PCs, e.g. Gmail, on WIndows & Mac, it does TOTP. It’s got a LastPass integration as well on mobile, too.
[link]