FC5: Manage Those Passwords!

Inventing good passwords is hard and so is remembering them, that’s part of the problem. So, how about we get computers to do the tedious stuff for us? Turns out you can, using something called a “Password manager”. Are these things going to end the Federation Conversation? [This piece is part of that conversation.]
Introduction · If you already use a password manager and know the basics, you can hop down to the Thought experiment section.
First: To those of you who have a lot of passwords and aren’t using a password manager, I’d say: Start now.
Second: If you’re wondering which to use, David Strom’s Best tools for protecting passwords is pretty good, even though it’s enterprise-focused and spends time on management options that I don’t care about.
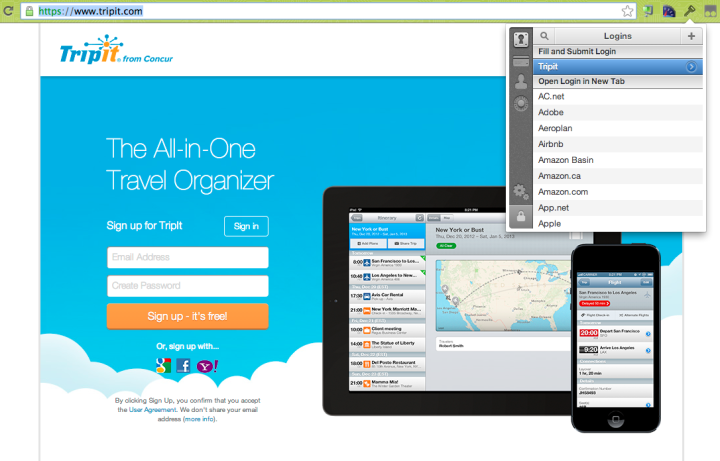
Third: Here’s what it looks like; a screenshot of me logging into the excellent Tripit travel organizer with the help of 1Password.
There’s a Chrome extension, so I click on the key, I type my master password, and 1Password is smart enough to notice that I’m at tripit.com and preselect that account, so I can click on that and my username and password are filled in just like that.
1Password sets a timer, so that if I go back for another login within a few minutes, I don’t have to re-type the master password. But the timer’s pretty damn short, so I end up typing it a lot.
On mobile, the picture is less pretty. When I log into my bank on my Android, I have to leave the bank app, get the 1Password app running, laboriously type in my master password, find the entry for the bank, hit the “copy” button, switch back to the bank app, and hit the “paste” button. I’m assuming this will get better.
By the way, I should mention that the password managers nearly all can be used to store other important secrets like account numbers for banks and insurance companies.
How it works · Your passwords have to be stored somewhere. And the managers take a lot of different approaches. For example, 1Password encrypts ’em all using your master password, and stores that on your DropBox. But there are lots of different approaches, and this matters, so I think providing a summary would be a mistake. Before you adopt a password manager, go and find out exactly how it’s going to manage them.
Thought experiment · Suppose everyone used a password manager. At the moment, a lot of non-geeks just won’t because the user experience isn’t good enough. But suppose we fixed that, made it totally slick — I saw a demo of a YubiKey making it a lot less painful on an Android device, so I think things will get better.
In that world, do we need Federated sign-in?
I totally approve of password managers; but I’m still not sure they’re the One True Path to reducing sign-in pain. The rest of this piece will mostly cover password-manager downsides, but once again: That doesn’t mean that I don’t think you should use one. You should.
The post-password era · To get money out of the bank, you need a piece of plastic and four digits. That’s because security pros have long since decided that the something-you-know/something-you-have combo generally trumps passwords in terms of user experience and security. So I suspect that a higher and higher proportion of the times you authenticate, you’re going to use something other than a password; check out the work of the FIDO Alliance. Which means that password managers solve a smaller and smaller piece of the puzzle.
Password paranoia · Now we all know that the spooks (both your own country’s and your country’s enemies’) are watching whatever they can and (more worrying) leaning on tech companies to install back doors, duplicate keys, and otherwise compromise your security.
This is one of the reasons why people worry about Federated sign-in with an IDP: “The spooks might be watching!” And yeah, they might; although the big Internet companies say repeatedly that they only respond to specific warrants.
But then, most password managers are closed-source commercial offerings, and you know what? The spooks can come after them, too. I’d say more but I don’t need to because the 1Password people wrote it up in totally clear no-bullshit language, in On the NSA, PRISM, and what it means for your 1Password data and a follow-up on Quora: “Is it reasonable to assume that developers of popular password management software (LastPass, ...) are/will be forced by law enforcement to install backdoors in their encryption algorithms?” Go read them.
Password expertise · Using a password manager supports you in choosing unique, high-quality passwords. But it doesn’t support the sites you’re signing into in doing a good job of authenticating you, watching for abusers and crooks and spooks, and protecting the passwords you send them.
If you care about that stuff (and you should), an IDP with a big team of dedicated security paranoids doing authentication starts to look better and better.
Take-away · A password manager reduces the probability that any one of your accounts will be hacked. And if one is, it reduces the probability that the information they get can be re-used elsewhere. Both of these are good things!
So yeah, go get a password manager and start using it. Bear in mind that even if Federated Identity becomes ubiquitous, you’re probably going to still have two or three different IDP passwords to remember, so let the manager take care of them.
But I don’t think this is a complete alternative to Federated sign-in, not even close.
Comment feed for ongoing:
From: David Singer (Sep 08 2013, at 13:03)
Ironically, when I went to read the answers on Quora, first it asked me to use Facebook or Google to identify me…and then it required me to create yet another password for Quora. *sigh*
Luckily, I use 1Password, so I'll never have to pay attention to that password, but….
[link]
From: Kevin Scaldeferri (Sep 08 2013, at 13:06)
I haven't see you address yet in this series the question: does Federated Sign-In improve the mobile experience, either now or in the future? I agree that the password manager experience on mobile is pretty painful, but how well does federated sign-in work currently? It doesn't seem like many app developers are choosing to use it.
[link]
From: Dan Scott (Sep 08 2013, at 13:32)
I'm glad you acknowledged that closed-source password managers (in particular those that conveniently centralize your accounts) are effectively no better that trusting a given idP, due to NSA-style interference.
I also concur completely with the concern over how poorly many sites are at password infrastructure.
There are the primary reasons that I trust in KeePassX / KeePassDroid as my password management solution. They are open source (and thus have auditable code: https://systemoverlord.com/portfolio/code-audit-keepassx/) and include random password generators that make it easy to maintain entirely distinct passwords for each site. At this point, I have over 400 accounts stored in my KeePassX password database.
Synchronization isn't perfect; while I maintain the database from my desktop via git, and in the past pulled copies from the git repo onto my Android device, these days I simply occasionally drop an updated copy of the database onto Google Drive from the desktop and use offline access on the Android side.
That said, I do take advantage of Google+ sign-in and Mozilla Persona in some situations. Long story short, I agree that a good password manager + a few idP is the most practical approach; and for the reasons outlined above, I think KeePass X/ KeePassDroid are the right choice of password manager.
[link]
From: anon (Sep 08 2013, at 13:46)
not sure how much idp will protect against bad sec in apps: if they fail to verify auth tokens correctly, as previously seen, we lose.
maybe a small class of abuse is now idp responsibility, but maybe that is offest by increased value of the idp
[link]
From: Jeremy Chatfield (Sep 08 2013, at 14:02)
I'm a contractor, working on multiple clients, sometimes in the course of a single day. I have many identities, as I often need to appear with an email address from my current client. Password Managers save me. Federated accounts don't - or not as they are usually envisaged by their developers. The assumption that I am one identity is true at the level of a State, but not true at the level of employment; things I do under one employment identity may not be applicable to, and should not be tied to, other employment identities. I think... probably... Anyway, for now, I try to maintain them as separate, and it's a minor pain (mobile phone apps particularly assume that I have one identity, and make it annoyingly hard to switch between them).
Mac OS X Maverick, and I believe the matching IOS, will be supporting an integrated password manager, synching between devices. And that integration should ease the current multi-screen frenzy you observe with 1Password. If they've done it the way that I hope (I haven't looked), then it'll be a API to authenticated apps, which means we can keep 1Password and still reap benefits (i.e. using it on Windows, when necessary). I haven't seen any discussion of that... but I haven't looked for it, either ;)
1Password is currently my favoured tool, except on the Chromebook, where I have to use pure browser plugin service because the 1Password app that the plugin uses, can't be run on ChromeOS. Even Password Managers have some limitations. Though, strictly, there is a slightly clumsy access to 1Password on DropBox through an HTML UI, but it is not integrated into the browser via a plugin.
Good series. Thanks!
[link]
From: Dave Walker (Sep 08 2013, at 14:13)
Good article.
It's worth pointing out the difference between "single sign-on" and "password sync" at this point, as it's something which, in my experience, a lot of people don't get; "true" SSO has you entering your credentials once (to your IDP or passwd manager, in this case) and then not needing to enter them again, for the duration of your session (or, in this case, until the IDP's or passwd manager's timer times out), whereas "password sync" replicates your credentials across a bunch of things which demand login credentials. You still need to put your credentials in every time with this approach, but you can be assured they're all the same - and, of course, if any member of such a scheme gets hacked to the point where your credentials can be lifted, you're compromised on every other system in the scheme.
Sharp-eyed readers will note that I'm likening a password manager to an SSO mechanism, here; twist it around and I think the analogy just about holds up (with you being your own IDP for your own credentials), but it's an interesting one to argue, either way.
Also, there's probably scope for another post looking to the (very) near future / unevenly-distributed present of wide deployment of authentication mechanisms other than passwords; I'd recommend a squint at http://www.lightbluetouchpaper.org/2012/05/22/the-quest-to-replace-passwords/ , on this front.
[link]
From: Tom Malaher (Sep 08 2013, at 15:51)
LastPass for Android installs an "input method" (aka keyboard), which will "type into" password fields for you.
This works with web sites quite well (it will preselect the correct password). Less well with apps (it recognizes most of them as "android.com" for some reason). But still less painful than copy/paste.
[link]
From: John Roth (Sep 08 2013, at 17:43)
I'm continually bemused by the blanket assumption that people can't remember good passwords. It simply takes some memory training. See http://en.wikipedia.org/wiki/Art_of_memory
It seems to be a giant hole in our collective knowledge base that it's never mentioned in discussions of good password discipline.
Combined with a good method of generation passphrases, such as diceware, it's at least as secure as any password manager, although not as convenient.
It is, however, utterly incompatible with federated identity, which puts all the eggs in one basket, and doesn't really allow you to create different passwords for different services.
[link]
From: John Cowan (Sep 08 2013, at 20:22)
"There are the primary reasons that I trust in [X] as my password management solution. They are open source and include random password generators that make it easy to maintain entirely distinct passwords for each site."
But you are assuming that encryption that protects those passwords has not already been compromised, which is very improbable. By the time an encryption algorithm is published in the open literature, methods of breaking it are most likely already known to the world's various spooks. This cannot be proved, but they certainly have an enormous incentive to do so, and there is no need to assume back doors or collaboration, just superior knowledge and motivation.
[link]
From: rosco (Sep 09 2013, at 03:55)
I have a text file with all my passwords in it. This lives in a small TrueCrypt container. I sync the container between my desktop and laptop computers with BitTorrent Sync (a bit like Dropbox). When I need a password I just mount the container and copy the relevant password. The TrueCrypt container password is my 'master password'. It's the simplest thing in the world and I wonder what all the fuss is about, really. I generate my passwords with a script that brings up a screen of junk based on /dev/random and then I blindly move the mouse cursor around and pick the fifteen characters that follow my blind click. I don't trust the security of mobile phones at all so I don't use anything on my phone that needs a password except email, which stores the password built-in. My phone has a keypad lock and is supposedly encrypted storage. I don't envy people that have complicated scenarios that require complicated solutions but it's sure interesting reading about it. Nice series of posts - very thought provoking - and my life may soon become complicated enough that I need to employ a more complex strategy.
[link]
From: Matěj Cepl (Sep 09 2013, at 04:16)
I think it would be worthy to evaluate already existing password managers built-in browsers. I still believe that Firefox Password Manager (together with their Sync) is worthy alternative (if one is willing to be bound to the Mozilla universe) and I haven't seen it mentioned anywhere.
[link]
From: rosco (Sep 09 2013, at 20:15)
(at Matěj) Yes, Mozilla Sync is wonderful. I should have mentioned that I use it between my laptop and desktop computers. My passwords file that I manually maintain is my 'master copy' and where I keep other details such as which email address or other details I have given to a website. The Mozilla Sync apparently does the encryption locally on each device and synchronises an encrypted password database between devices and also a server. I feel secure knowing that my passwords are encrypted on the server and only I hold the keys on my local devices. Mozilla seems to have that nailed this. I also have Firefox browser on my phone but don't synchronise it because I don't do anything on my phone that needs login. Careful: It is easy to accidentally delete all of your stored passwords in Firefox and then the deletion is propagated to all devices - so always keep your own master copy and don't totally rely on Mozilla Sync by itself.
[link]